Last updated March 2023
Beginning as early as 2014, Starwood hotels, now owned by Marriott, experienced a massive credit card data breach reportedly at the hands of Chinese hackers. The data breach may have exposed the personal information of as many as 500 million guests of the hotel chain.
Impact of a Credit Card Breach
Once the news of this breach became public, the far-reaching costs began showing almost immediately.
According to Forbes, “The company now faces a class-action suit and shares have subsequently fallen 5.6%. On top of this, Marriott says for about 327 million victims, compromised data may include names, addresses and passport numbers — prompting Senator Chuck Schumer to demand that it "foot the bill" for new passports.”
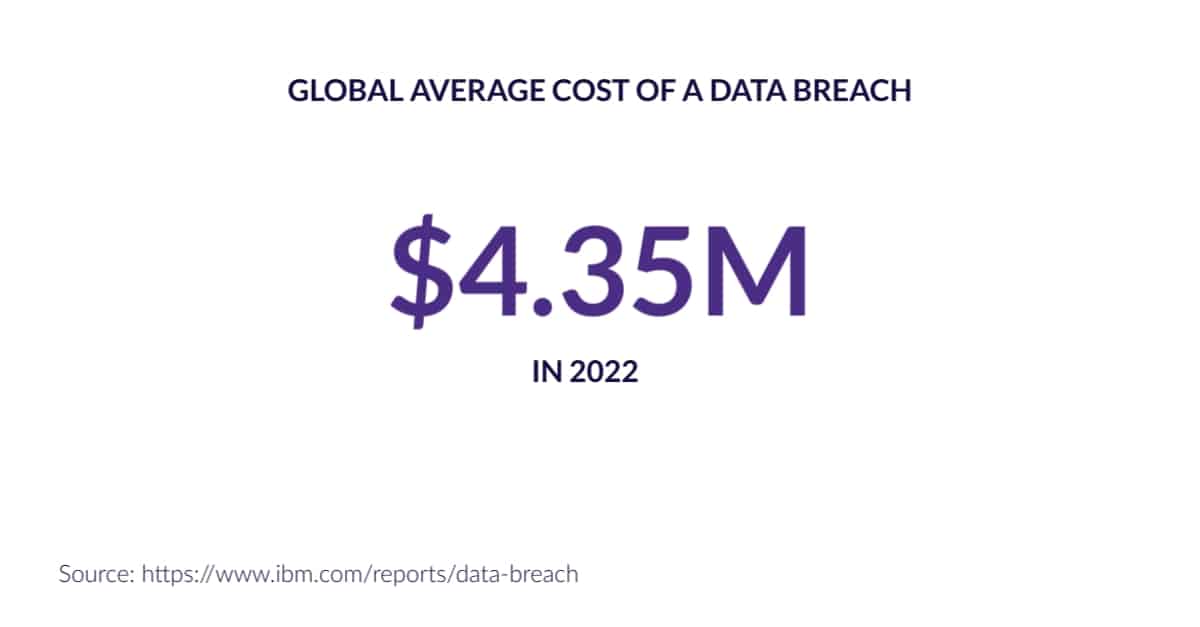
Not all costs of a security breach translate directly to a dollar amount. NBC News illustrates some of the other struggles companies face after their systems have been invaded.
“Aside from expensive technical investigations and regulatory filings, a breach also includes hidden costs such as lost business, negative impact on reputation, and employee time spent on recovery, according to a new report by the Ponemon Institute.”
The reputation hit is being felt in this example. Marriott didn’t acquire Starwood until 2016, in the midst of the breach. But in the eyes of the public, this fact doesn’t excuse Marriott from fault.
“In news reports, this is not Starwood’s data breach, but Marriott International’s,” says an article on the Internet Society. “Like any data breach, this incident will harm trust between the company and its customers.”
The same article explains why this happening on Starwood’s watch doesn’t matter.
“When Marriott International acquired Starwood and its data, they also acquired the risk associated with storing and handling that data. Digital security is a crucial part of a corporation’s bottom line, and security incidents can quickly become disastrous for a business.”
“Organizations can take steps that will significantly reduce the overall cost of a data breach. Things like having an incident response team, having the right governance process in place, having enabling technologies. All of these basic blocking and tracking activities makes a difference in terms of cost.”
PONEMON INSTITUTE
What Should Merchants Know About Credit Card Security Standards
At Marriott’s size, the company will likely bounce back from this breach. Smaller businesses may not be so lucky. That’s why Payment Card Industry Data Security Standards (PCI DSS) exist.
These credit card compliance rules are intended to protect the sensitive card data that is used in processing a payment. Depending upon a company’s size, it must adhere to one of four PCI compliance levels.
The more transactions a company processes each year, the more stringent its credit card compliance burden becomes.
However, if a company is subject to a credit card breach, it may not be able to withstand the reputational losses companies like Marriott have experienced. This is especially true if the business in question relies on other businesses as clients. No management team will feel comfortable entering into a contract with a company that isn’t adequately protecting sensitive credit card data.
Visa pci compliance requirements
PCI Compliance Level
Level 1:
Merchants processing over 6 million Visa transactions annually across all channels.
PCI Requirements
Every year:
- File a Report on Compliance {ROC) by a Qualified Security Assessor (QSA) or internal auditor if signed by an officer of the company.
- Submit an Attestation of Compliance (AOC) form.
Every quarter:
- Conduct a quarterly network scan by an Approved Scan Vendor (ASV).
PCI Compliance Level
Level 2:
Merchants processing 1 to 6 million Visa transactions annually across all channels.
PCI Requirements
Every year:
- Complete a Self-Assessment Questionnaire (SAQ).
- Submit an Attestation of Compliance (AOC) form.
Every quarter:
- Conduct a quarterly network scan by an Approved Scan Vendor (ASV).
PCI Compliance Level
Level 3:
Merchants processing 20,000 to 1 million Visa ecommerce transactions annually.
PCI Requirements
Every year:
- Complete a Self-Assessment Questionnaire (SAQ).
- Submit an Attestation of Compliance (AOC) form.
Every quarter:
- Conduct a quarterly network scan by an Approved Scan Vendor (ASV).
PCI Compliance Level
Level 4:
Merchants processing less than 20,000 Visa ecommerce transactions annually and all other merchants processing up to 1 million Visa transactions annually.
PCI Requirements
Every year:
- Complete a Self-Assessment Questionnaire (SAQ).
- Submit an Attestation of Compliance (AOC) form.
Every quarter:
- Conduct a quarterly network scan by an Approved Scan Vendor (ASV).
Though scans are listed for every level of compliance, they are not required depending upon the Self Assessment Questionnaire (SAQ) each business must complete.
According to complianceguide.org, regular scans are required for SAQ A-EP, SAQ B-IP, SAQ C, SAQ D-Merchant and SAQ D-Service Provider.
There are two instances where merchants are eligible for the simple SAQ A:
- "Merchant website is entirely hosted and managed by a PCI-compliant, third-party payment processor, OR"
- "Merchant website provides an iframe or URL that redirects a consumer to a PCI-compliant, third-party payment processor, where no elements of the page originate from the merchant website."
How to Manage Your Sensitive Credit Card Data
CREDIT CARD COMPLIANCE POLICIES
Ensure business policies are sufficient to keep data safe and are in line with PCI data security standards. The policies and procedures should be kept as part of the company’s larger compliance management system.
They can be updated after issues by conducting a root cause analysis or can be audited and updated in larger segments as needed.
Many merchant service providers also host a PCI certification program for their merchants with national vendors like Trustwave and Security Metrics. These programs provide all the policy and procedure templates your business needs to pass credit card compliance standards.
EMPLOYEE EDUCATION/TRAINING
Of course, setting PCI data protection policies within your company is necessary. But policies won’t be helpful if they aren’t being followed. Providing initial education and ongoing training opportunities to staff helps you to prepare your staff for properly handling sensitive cardholder data, including:
- Cardholder names
- Credit card numbers
- CVV information
THIRD-PARTY PAYMENT PROCESSORS AND WHAT YOU NEED TO ASK
Merchants need to understand the burden their core account management software holds in regard to credit card data security. Account management software should be PCI-PA (payment application) compliant. If they are, credit card numbers can pass through their system to the payment processor. If their software isn’t compliant, then the merchants that use it aren’t compliant either.
As a business owner using third-party vendors for services, consider what your clients might ask about your credit card payment compliance.
Ask third-party payment processors what happens to credit card numbers once service is established. Credit card tokenization is the act of creating a placeholder (token) to represent each customer's credit card number. Merchants who only have access to a token will lose all recurring payment schedules created through that processor if they wish to leave.
If you want the freedom to switch merchant service providers without disrupting your day-to-day business, find payment processing software that maintains both credit card numbers and tokens.
How PDCflow Protects Its Integration Partners and Software Clients
SECURE ENTRY OVERLAY
PDCflow supports your credit card compliance by using a patented technology that protects both our clients and our software integration partners. Secure Entry Overlay technology eliminates merchant and software partner need for contact, transmission or processing of a credit card number.
PDCflow’s protected process provides a small data entry window that is directly connected to our PCI certified environment. This window is where a credit card number is entered. The ability to input card numbers directly into our PCI certified environment reduces our client’s PCI scope.
Our software integration partners gain the most protection. With Secure Entry Overlay, their software is completely eliminated from the scope of PCI compliance because it never touches a credit card number.
LEVEL 1 PCI COMPLIANCE
The highest level of PCI compliance is a costly and labor-intensive investment. PDCflow has taken on this burden so that taking credit card payments becomes safer for our customers. We use a third-party audit of our facilities, programming, and infrastructure performed by a professional certification auditor.
By maintaining Level 1 PCI DSS compliance, we ensure an extra level of protection for our clients and their consumers.